How to create a secure passwordtips and tricks to protect your online accounts from hackers and malicious attackers.
La computer security is a vitally important topic that, unfortunately, is rather underestimated. It is not uncommon to hear of hacked profiles and accounts, with private information being stolen from the unfortunate, sensitive data that can ruin a person's life. Therefore, as online threats increase, the creation of secure passwords becomes a key factor to protecting our personal data.
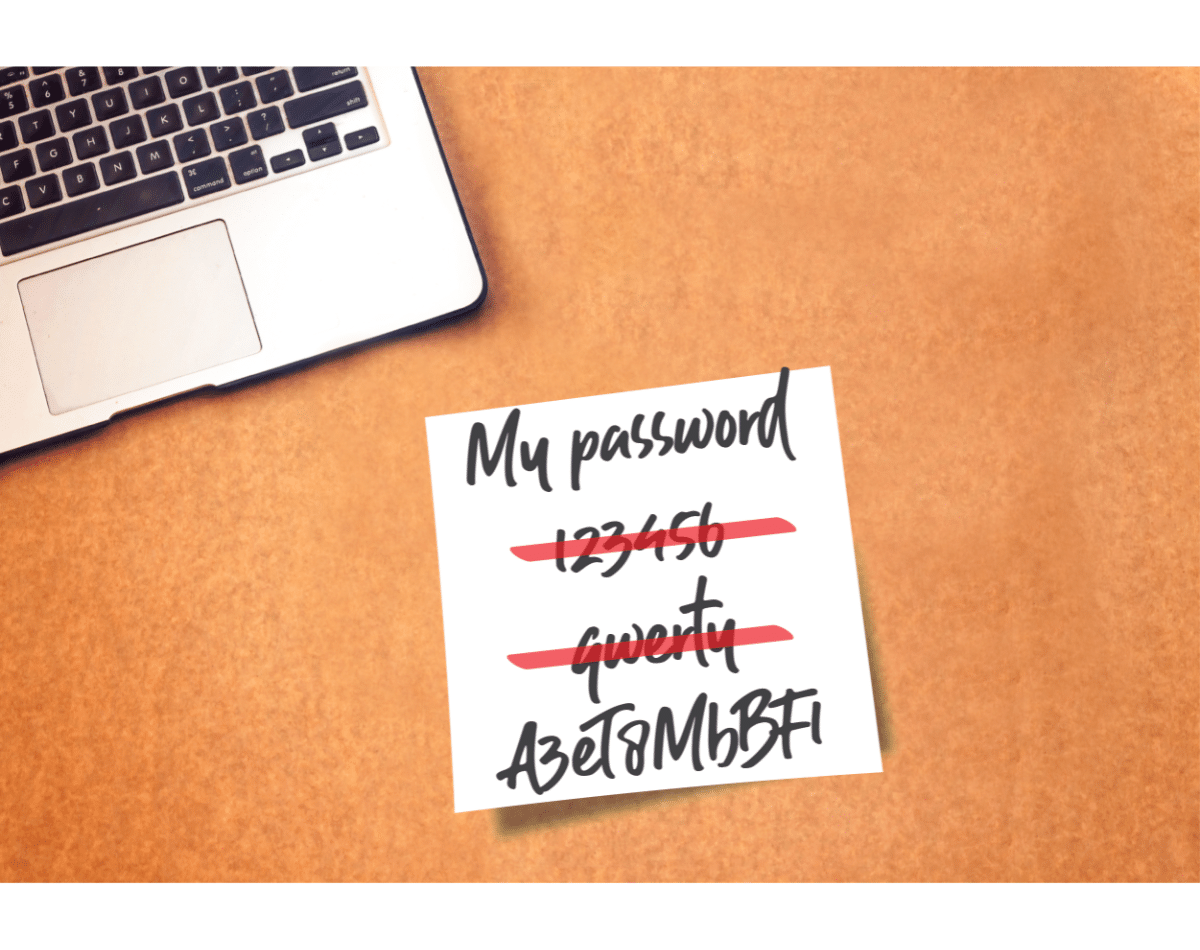
The password is the main authentication mechanism used to access our online accounts. However, many people use simple and very easy-to-guess solutions, such as '123456' or their date of birth, thus becoming easily predictable and vulnerable to attacks by cyber criminals. This makes it child's play to breach the security of our profiles. Let us therefore see how to create a secure and effective password.
How to create a secure password
To generate a secure password, it is important to follow some basic guidelines:

- in the first place should be complex and not easily guessed. This means that it must contain a combination of upper and lower case letters, numbers and symbols. A good idea would be to choose a long, complicated sentence, using the first letters of each word to create the password.
- key is to choose a unique access key for each account. Never use the same for more than one account, because if it is hacked, all other profiles with the same password (be it the bank, the social media etc.) will be just as vulnerable.
- Another relevant aspect is the need to change it regularly. Even the most complex ones can be compromised, so it is a good practice to change them every three to six months, maximum one year.
- One must also avoid using personal information or easily accessible to create a password. For example, your name, date of birth, pet's name or other similar personal information that could be discovered very easily.
- Finally, it is important to use a good password manager programme that allows you to generate, store and manage passwords securely, preserving them thanks to the encryptionso that you do not have to memorise them all (read an article on the features of a password manager here).
Secure passwords examples
If you do not know how to create a secure password, here are some interesting examples (please note that these are only references):
- Home1234#Vento
This password consists of 14 characters, using a combination of upper and lower case letters, numbers and symbols, characterised by random words that are not easy to guess. The presence of symbols and numbers increases the complexity and makes it more difficult to guess or decipher.
- 9J#fM7cH@5nRtK
Unlike the previous one, we can observe a totally random sequence of characters that do not form common words, making it difficult for a potential intruder to guess the password.
- Cr34reUn4P@ssw0rdS1cur4!
Here is the original sentence how to create a secure password was changed by replacing some letters with numbers and adding symbols to make the password more complex and difficult to crack.
How do attackers steal your codes?
We have seen how to create a secure password, but you may have wondered how cybercriminals get hold of your data, especially 'passwords'.
Hackers use various techniques, and among the most basic ones we can mention the dictionary attackin which software is used that attempts to guess an account password using a list of common words or phrases frequently used by users. In this way, the hacker can gain access to the account by breaking the user's password. It may sound far-fetched, but still many people use solutions such as 'home1', 'password1', 'hello1' and so on.
Another common method is the phishingin which the hacker sends a fraudulent email to the user with a link to a fake web page that imitates a legitimate website. The user is then tricked into entering their login credentials, such as username and password, on the fake web page, allowing the hacker to acquire this login information.
We can then mention the use of malwaremalicious software that installs itself on the user's computer and records the access information entered by the user, or the database violation of a company, which can lead to the exposure of user passwords.
Conclusion
In summary, regarding how to create a secure password, it is essential to follow these basic guidelines in order to protect one's digital identity and personal data. A weak and easily hackable password can lead to serious consequencessuch as identity theft, financial fraud or damage to online reputation.
For this reason, it is important to use a secure and unique password for each account, to avoid using common or easily guessable words, and to beware of phishing or social engineering attempts.